Deloitte Cyber Security Quiz-2
Analytics below shows your performance in various Mocks on PrepInsta
Your average Analytics for this Quiz
Rank
-
Percentile
0%
Related Banners
Check out our instagram

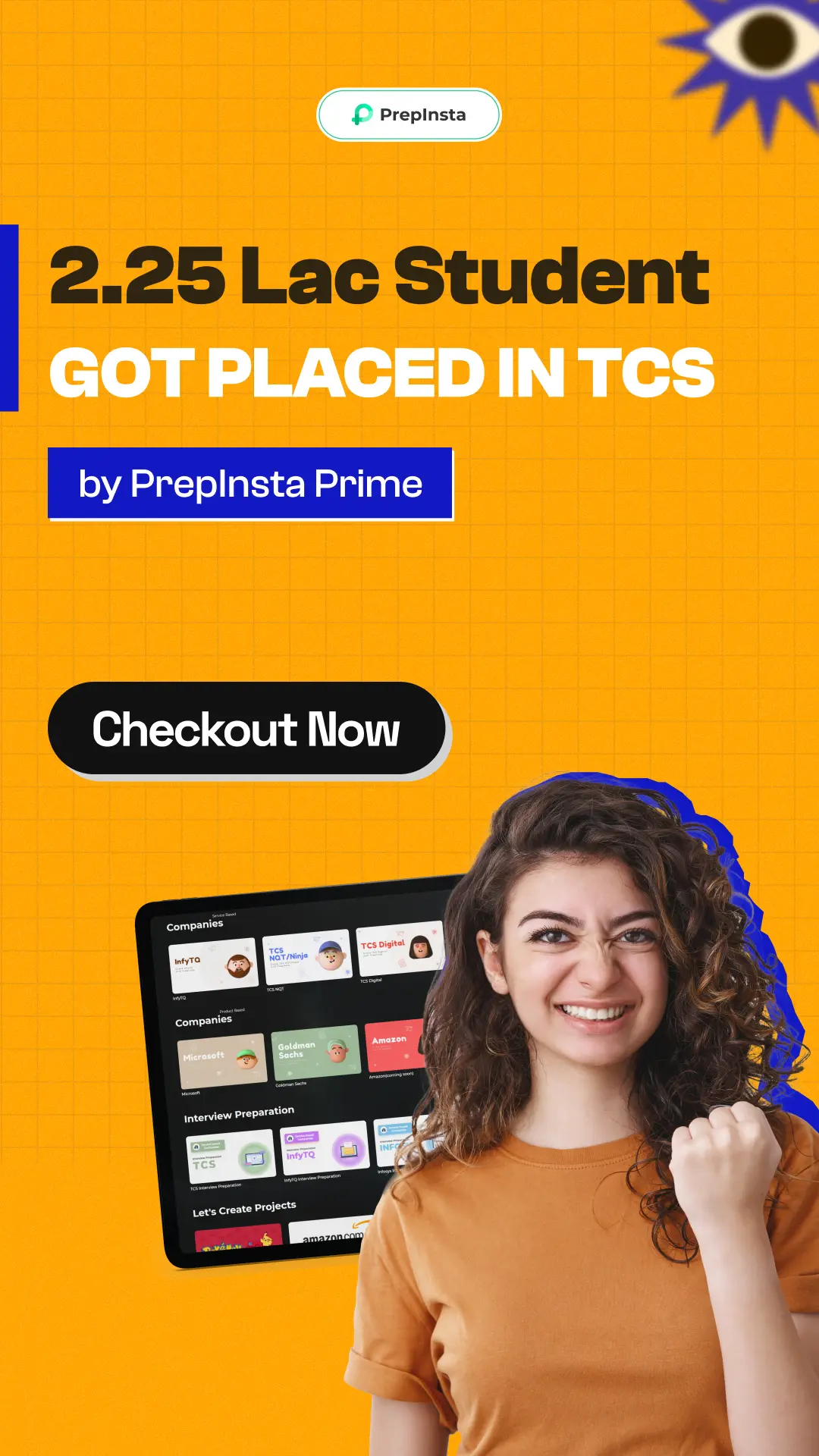
PrepInsta Prime
Get over 200+ course One Subscription

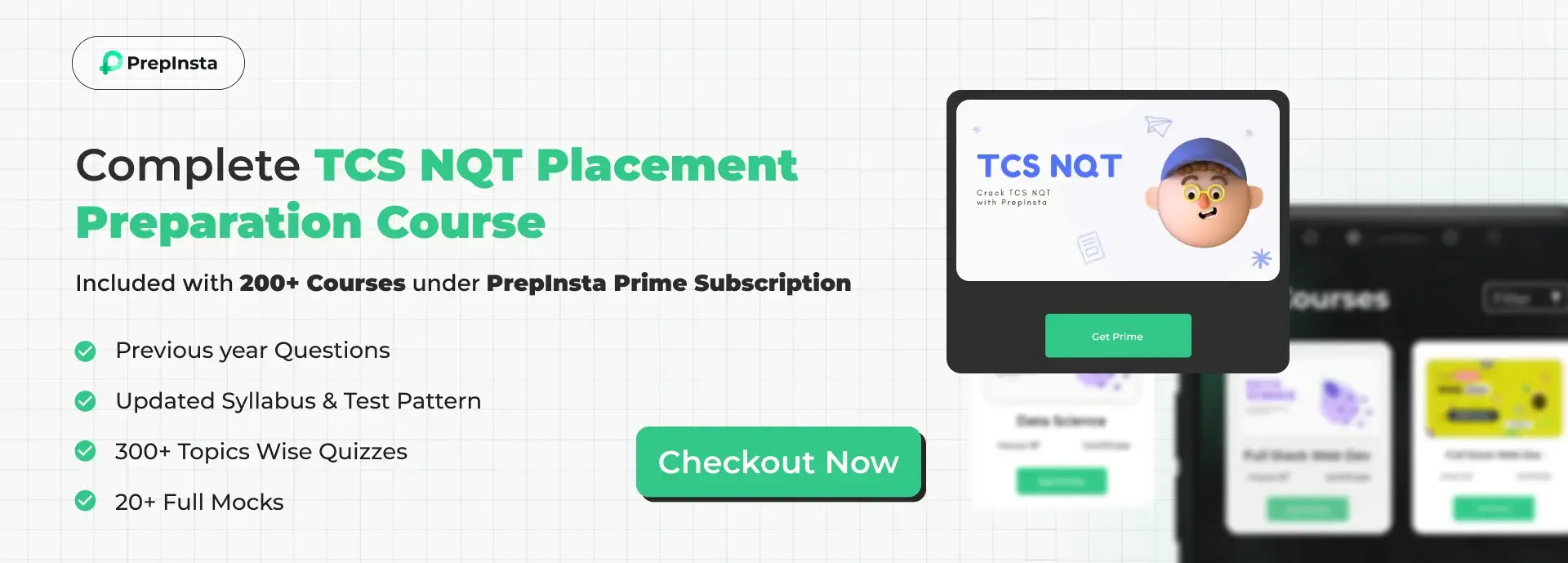
PrepInsta Prime
Get over 200+ course One Subscription
Get PrepInsta Prime Subscription
Companies
TCS, Cognizant, Delloite, Infosys, Wipro, CoCubes, KPMG, Amazone, ZS Associates, Accenture, Congnizant & other 50+ companies
Programming
Data Structures, Top 500 Codes, C, C++, Java Python & other 10+ subjects
Skills
Full Stack Web Development, Data Science, Machine Learning, AWS Cloud, & other 10+ skills and 20+ projects
Companies
TCS, Cognizant, Delloite, Infosys, Wipro, CoCubes, KPMG, Amazone, ZS Associates, Accenture, Congnizant & other 50+ companies
Programming
TCS, Cognizant, Delloite, Infosys, Wipro, CoCubes, KPMG, Amazone, ZS Associates, Accenture, Congnizant & other 50+ companies
Skills
TCS, Cognizant, Delloite, Infosys, Wipro, CoCubes, KPMG, Amazone, ZS Associates, Accenture, Congnizant & other 50+ companies

 0
0




 Instagram
Instagram Whatsapp
Whatsapp Telegram
Telegram Linkedin
Linkedin