0
Notifications Mark All Read
No New notification
- Login
- Get Prime
How to become an Ethical Hacker in 2023?
Ethical Hacking Roadmap: A Complete Guide
In this page we will tell you about How to become an Ethical Hacker in 2023? Ethical Hacker, also known as a white-hat hacker or penetration tester, involves acquiring technical skills, ethical understanding, and relevant certifications.
Table of Content :
- What is ethical Hacking?
- Objective or Role of an ethical Hacker.
- Complete Roadmap to become an Ethical Hacker.
- Skills/ Tools required to be an Ethical Hacker.
- Job role of an ethical Hacker.

What is Ethical Hacking?
It is the practice of identifying vulnerabilities and weaknesses in computer systems, networks, applications, or other digital assets with the permission of the owner. Ethical hackers use their skills and knowledge to assess the security posture of an organization’s systems and provide recommendations for improving their security defenses.
Objective or Roles of an Ethical Hacker
The primary objective of ethical hacking is to simulate real-world attacks and help organizations proactively identify and address vulnerabilities before malicious hackers exploit them. By conducting authorized hacking activities, ethical hackers help protect sensitive information, prevent data breaches, and ensure the overall security of an organization’s digital infrastructure.
Roles of an Ethical Hacker :
Observation : Gathering information about the target system or organization through public sources, network scanning, or social engineering.
Vulnerability assessment : Identifying security vulnerabilities, weaknesses, or misconfigurations in networks, operating systems, web applications, or databases.
Exploitation: Attempting to exploit the identified vulnerabilities to gain unauthorized access or escalate privileges within the system.
Post-exploitation: Assessing the impact of successful attacks and identifying further security risks or potential damage.
Reporting: Documenting the findings, providing detailed reports on vulnerabilities discovered, and offering recommendations to address and mitigate the identified security issues.
To know more about Ethical Hacking course, Click on the link given below
Skills required to become an Ethical Hacker
- Knowledge of Computer Networks
- Programming
- Web Application
- Data Base
- Ethical Hacking Tools
- Knowledge of common attack and vectors techniques
- Certificates
Complete Roadmap to become an Ethical Hacker
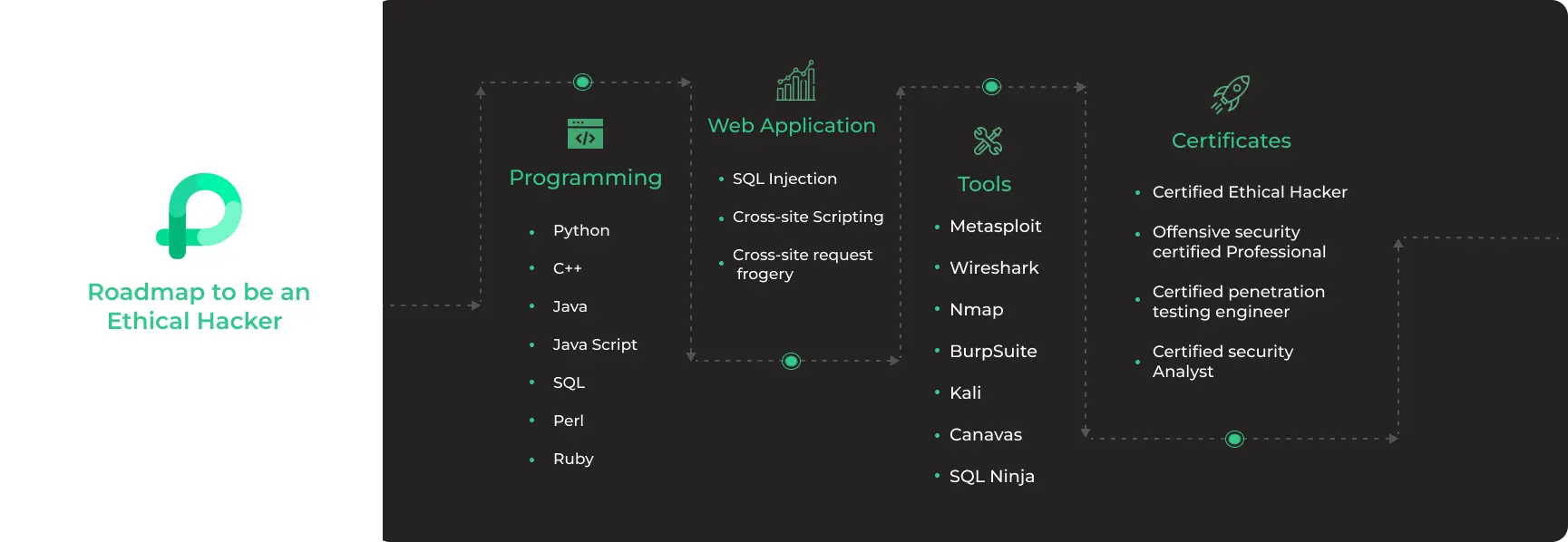
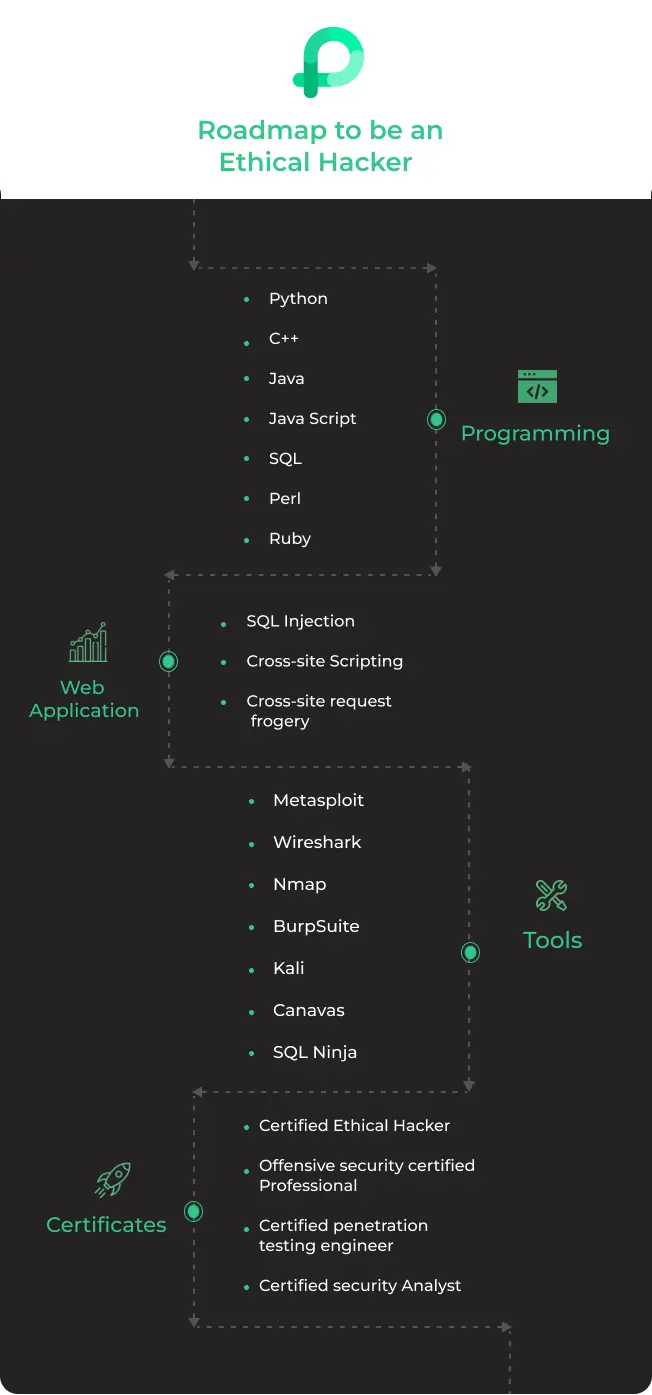
9 Steps to Become an Ethical Hacker in 2023
Knowledge of computer systems and networks:
Understand the functioning of computer systems, network protocols, operating systems, and how various components interact within a networked environment.
Proficiency in programming languages :
Gain expertise in programming languages like
Networking and security concepts :
Familiarize yourself with the principles of computer networking, network security, and different security protocols. Understand how data is transmitted, secured, and protected in a networked environment.
Web application and database knowledge :
Develop an understanding of web application architectures, web protocols, and database systems. Learn about common vulnerabilities specific to web applications such as :
Understanding of operating systems:
Develop expertise in different operating systems, such as Windows, Linux, or macOS. This includes understanding system configurations, permissions, and security mechanisms specific to each operating system.
Familiarity with ethical hacking tools :
Gain experience and knowledge with popular ethical hacking tools like :
Problem-solving and analytical thinking :
An Ethical hackers need to possess strong problem-solving skills and the ability to think analytically. You should be able to analyze complex systems, identify vulnerabilities, and devise effective strategies to mitigate potential risks.
Knowledge of common attack vectors and techniques :
Understand various hacking techniques and attack vectors used by malicious hackers, such as social engineering, phishing, password cracking, or network-based attacks. This knowledge helps you anticipate and prevent potential threats.
Certifications :
Certifications are not such a big thing to start your Ethical Hacking career. But the skills will provide you a great leaning path also these certificates describes your understanding of hacking techniques.
Job Roles of Ethical Hacker
There are several job roles in Ethical Hacking such as :
- Ethical Hacker
- Network Security Engineer
- Cyber Security Analyst
- Penetration Tester
- Information Security Manager
- Cyber security Engineer
- Security Consultant
Salary of an Ethical Hacker depends upon the job role given above. To know more about salaries of different Ethical Hackers, click on the link given below
FAQ's on How to become an Ethical Hacker in 2023
What are the types of hacker?
There are three types of hacker:
- White hat
- Black hat
- Grey hat
Where does Ethical hacker work?
Ethical Hacker work in several industries like
- Software companies
- Hardware companies
- Government Institution
What is the difference between ethical hacking and malicious hacking?
The key difference between ethical hacking and malicious hacking lies in the intent and legality. Ethical hacking is performed with the explicit permission of the system owner, with the goal of identifying vulnerabilities and improving security. It is a legal and authorized activity. On the other hand, malicious hacking is unauthorized and aims to exploit vulnerabilities for personal gain, damage, or illicit activities. Malicious hacking is illegal and punishable by law.
What is a firewall?
A firewall is a network security device or software that acts as a barrier between a trusted internal network and an untrusted external network (such as the internet). It monitors and controls incoming and outgoing network traffic based on predetermined security rules.
Get over 200+ course One Subscription
Courses like AI/ML, Cloud Computing, Ethical Hacking, C, C++, Java, Python, DSA (All Languages), Competitive Coding (All Languages), TCS, Infosys, Wipro, Amazon, DBMS, SQL and others

 0
0
Login/Signup to comment