Tech Mahindra Menu
- Previous Papers
- Tech Mahindra Syllabus
- Quantitative Aptitude
- Verbal English
- Logical Ability
- English Essay
- Conversational Assessment
- Computer Science
- Computer Programming
- Super Coder
- Coding
- Tech Test
- Personality Test
- Tech Mahindra Eligibility Criteria
- Tech Mahindra Recruitment Process
- Interview Questions
PREPINSTA PRIME
Tech Mahindra Technical Interview Questions
Tech Mahindra Technical Interview Questions and Answers 2025
Read the most important technical questions asked recently in the Tech Mahindra Technical Interview 2025.
Page Highlights:-
- Tech Mahindra Test Pattern
- Tech Mahindra Technical Interview Questions
Tech Mahindra Test Pattern
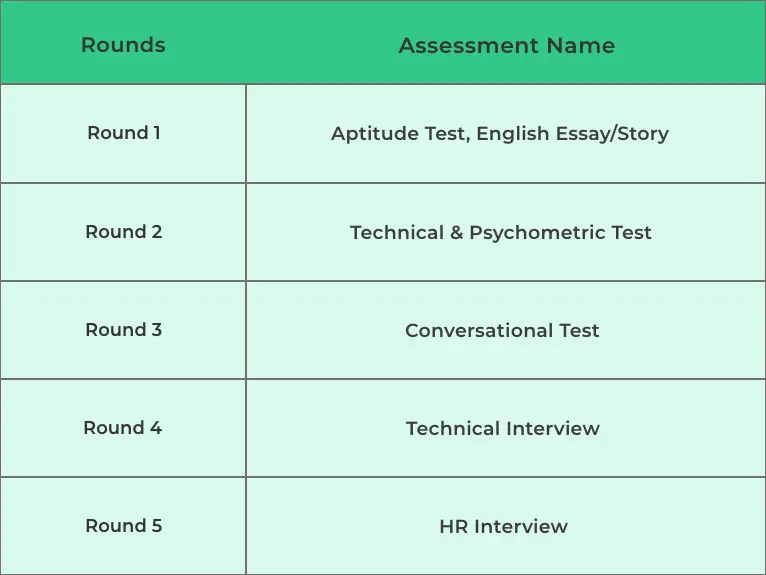
Tech Mahindra Technical Interview Questions
Question 1: What do you mean by normalization?
Answer:
Normalization: Data in a database are organized through a process called normalization. This comprises the creation of tables and the establishment of linkages between those tables in accordance with rules aimed to secure the data and make the database more adaptable by removing redundancy and inconsistent dependence.
Question 2: Define: stack, queue, array, and linked list.
Answer:
Stack: A stack is a linear data structure that is represented by a fixed sequence of elements.
Queue: A queue is a collection of items that are added and withdrawn in accordance with the first-in, first-out (FIFO) principle.
Array: An array is a group of connected data values known as elements, each of which is designated by an index array.
Linked list: A linked list is the most widely used data structure for handling dynamic data items. A linked list is made up of data elements known as nodes.
There are two fields on each node:
- One field contains data.
- The node holds a reference to the next node in the second field.
Question 3: What do you mean by 3NF in DBMS?
Answer:
The third normal form (3NF) is a relational database schema design technique that uses normalizing principles to decrease data duplication, prevent data errors, guarantee referential integrity, and streamline data maintenance.
Questions 4: What are the four different storage classes available in C?
Answer:
The following are the four different storage classes available in C:
- Register
- Auto
- Extern
- Static
Question 5: Define the operating system.
Answer:
An operating system is a type of software that manages files, memory, processes, input, and output, and controls peripheral devices, among other fundamental duties.
Question 6: What are pointers?
Answer:
A variable that contains the address of another variable of the same type is known as a pointer. The value of the variable to which the pointer points is obtained by dereferencing it using the * operator. There are various kinds of pointers, including null, void, wild, and others.
Question 7: Write a Java program to remove characters in a string except for alphabets.
class Main
{
// function to remove characters and
// print new string
static void removeSpecialCharacter(String s)
{
for (int i = 0; i < s.length(); i++)
{
// Finding the character whose
// ASCII value fall under this
// range
if (s.charAt(i) < 'A' || s.charAt(i) > 'Z' && s.charAt(i) < 'a' || s.charAt(i) > 'z')
{
// erase function to erase
// the character
s = s.substring(0, i) + s.substring(i + 1);
i--;
}
}
System.out.print(s);
}
// Driver code
public static void main(String[] args)
{
String s = "$P*r;e..pi, ns'ta^?";
removeSpecialCharacter(s);
}
}
Question 8: What do you mean by structured programming?
Answer:
Structured Programming is a programming paradigm in which the control flow is completely structured. A structure is a block that has a set of rules and a defined control flow. Structured programming is utilized in almost all programming paradigms, including the OOPs model.
Questions 9: Write a program to check whether or not a number is automorphic no. in python.
number = 376
square = pow(number, 2)
mod = pow(10, len(str(number)))
# 141376 % 1000
if square % mod == number:
print("It's an Automorphic Number")
else:
print("It's not an Automorphic Number")
Question 10: How is a call by value different from a call by reference?
| Parameters | Call by value | Call by Reference |
|---|---|---|
| Basic | A duplicate of the variable is passed. | The actual variable is passed. |
| Effect | The original value of a variable is unaffected by changes to its duplicate. | The original value of a variable is altered when a duplicate of the variable is changed. |
| Syntax | function_name(a1, a2,……) where, (a=variable name) | function_name(&a1, &a2,….) where, (a=variable name) |
Question 11: Name some object-oriented programming languages.
Answer:
Some object-oriented programming languages are:
- Java
- C++
- Ruby
- Python
- TypeScript
- PHP
Question 12: Define a token.
Answer:
The smallest components of a program that have meaning for the compiler are called tokens. The various token kinds include the following:
- Keywords
- Identifiers
- Constant
- Strings
- Operators
Question 13: Write a C++ program to find the GCD of two numbers.
#includeusing namespace std; int main() { int n1 = 18, n2 = 45, gcd = 1; for(int i = 1; i <= n1 || i <= n2; i++) { if(n1 % i == 0 && n2 % i == 0) gcd = i; } cout<<"The GCD is "<< gcd; return 0; } // Time complexity : O(N) // Space complexity : O(1)
Question 14: Define Java Virtual Machine (JVM).
Answer:
The Java Virtual Machine, also known as JVM, loads, validates and runs Java bytecode. Because it executes Java code, it is referred to as the interpreter or the core of the Java programming language.
Question 15: What are the advantages of Java Packages?
Answer:
- The Java package is used to categorize classes and interfaces in order to make them easier to manage.
- The Java package protects against unauthorized access.
- A Java package eliminates naming conflicts.
Question 16: What is a checkpoint in DBMS?
Answer:
A checkpoint mechanism stores all previous logs permanently in a storage disc after removing them from the system. Checkpoint identifies a time period in which all transactions had been committed and the DBMS was in a consistent state.
Question 17: Define binary tree insertion.
Answer:
A binary search tree’s insert function is used to add a new element at the right spot. The insert function must be created in such a way that it violates the binary search tree’s property at each value.
Question 18: Define syntax and semantic errors.
Answer:
Syntax: Syntax errors are caused by faulty source code composition.
Semantic error: A semantic error is faulty reasoning that delivers the incorrect outcome when executed.
Question 19: Define skew trees.
Answer:
A skewed tree is one that either has one child node or none at all for each node.
Question 20: Write a C++ program to print the Fibonacci series up to N numbers.
#includeusing namespace std; int Fib(int n){ // Note : declaring static items too here static int t1 = 0, t2 = 1, nextTerm; if(n > 0) { nextTerm = t1 + t2; t1 = t2; t2 = nextTerm; cout << nextTerm << ", "; Fib(n-1); } } int main() { int n = 15; cout << "0, 1, "; // n-2 as 2 terms already printed Fib(n-2); return 0; }

 Apply For Jobs
Apply For Jobs Get Hiring Updates
Get Hiring Updates