Introduction to Hashing in Python

Introduction to Hashing in Python
Hashing is a fundamental concept used to efficiently store and retrieve data. Hashing algorithms play a crucial role in various applications, including data retrieval, encryption, and security.
Let’s jump into the article to know more about Hashing in Python and also you will get to know about the world of hashing, explaining its importance, different types, and practical applications.
Understanding Hashing in Python
Hashing is a process of mapping data of arbitrary size to a fixed-size value, known as a hash code or simply a “hash.” The primary objective of hashing is to expedite data retrieval by converting complex data into a compact representation, making it easier to manage and access.
Hashing in Python Examples
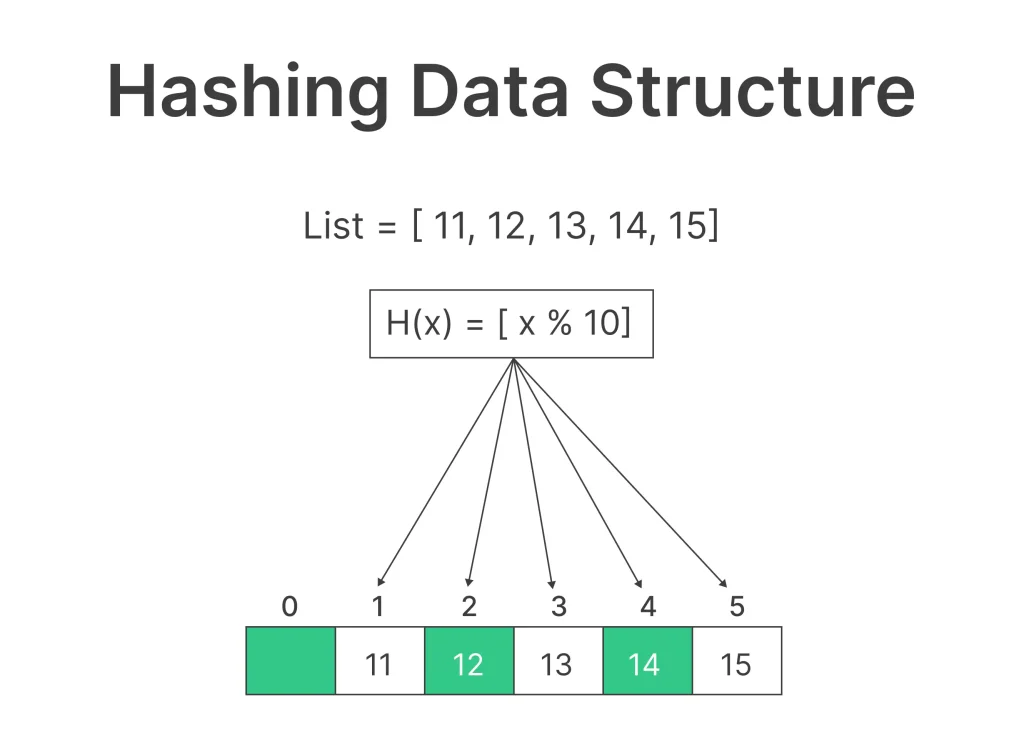
Why Use Hashing in Python?
Hashing in Python is widely used for various reasons, including data integrity, password storage, and efficient data retrieval. It allows for quick data comparison and indexing, making it a crucial tool for programmers.
Hash Function in Python
A hash function is a mathematical function that takes an input (or ‘message’) and returns a fixed-size string of characters, which is typically a hexadecimal number. The output, often called the ‘hash value’ or ‘hash code,’ is unique to the input data. Hash functions are designed to efficiently map data of arbitrary size to a fixed-size value.
Hashing in Python
- Python provides built-in hash functions, making it easy to compute hash values for data. Python’s
hash()function is often used for this purpose. However, in some cases, you may need to create custom hash functions tailored to your specific needs.
Prime Course Trailer
Related Banners
Implementing Hash Functions in Python
Python offers a built-in hash() function that can quickly compute hash values for a variety of data types.
Code :
# Hashing a string
data = "Hello, World!"
hash_value = hash(data)
print("Hash value for the string:", hash_value)
# Hashing an integer
number = 42
hash_value = hash(number)
print("Hash value for the integer:", hash_value)
Explanation :
- The hash() function is used to generate hash values for both a string and an integer.
- It’s important to note that the hash values produced by the hash() function are platform-specific and may differ between different Python installations.
- These hash values are suitable for data retrieval and data integrity checks, but they should not be used in security-sensitive applications like password hashing.
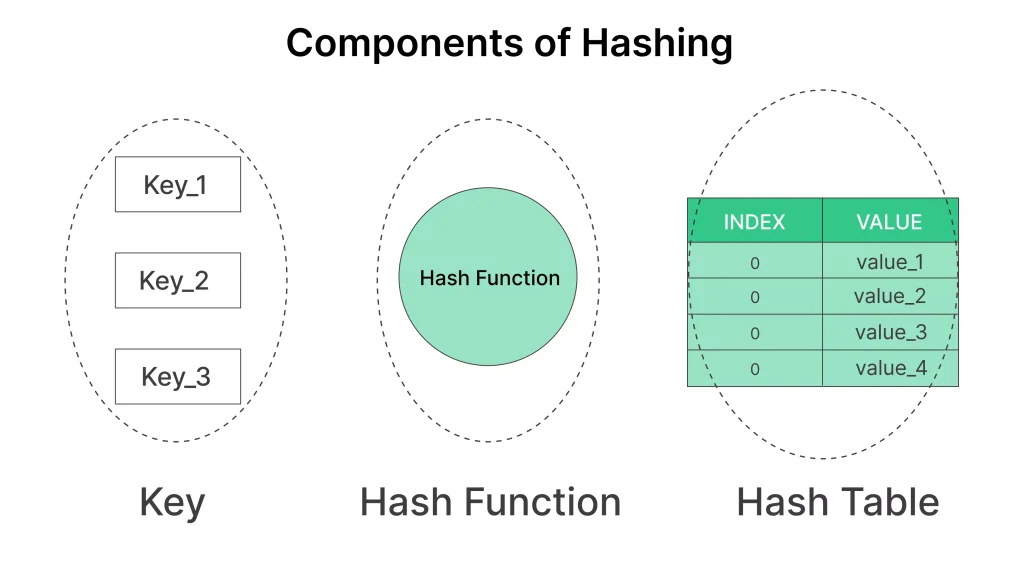
Components of Hashing in Python
Get PrepInsta Prime & get Access to all 200+ courses offered by PrepInsta in One Subscription
Hashing Algorithms in Python
Python supports several hashing algorithms, such as MD5, SHA-1, and SHA-256. These algorithms produce hash values of varying lengths and security levels.
Types of Hashing Algorithms:
- MD5
- SHA-1
- SHA-256
MD5
MD5, which stands for Message Digest Algorithm 5, is a widely used cryptographic hash function. It was designed by Ronald Rivest in 1991 and is commonly employed in various applications for data verification and fingerprinting. MD5 produces a fixed-size 128-bit (16-byte) hash value, typically represented as a 32-character hexadecimal number.
Common Uses of MD5
1. Data Integrity
MD5 is often used to verify the integrity of data during transmission. By computing the MD5 hash of the original data and comparing it with the received data’s hash, you can quickly detect any changes or errors.
2. Password Storage
MD5 was used to store passwords. When a user creates or updates a password, the system hashes it using MD5 and stores the hash. When the user logs in, the system hashes the entered password and compares it to the stored hash.
3. Digital Signatures
MD5 is employed in digital signatures and certificates to ensure the authenticity of documents and software. By hashing the content and providing a hash value, you can verify that the document has not been altered.
import hashlib
# Input string
data = "hello world"
# Creating MD5 hash object
md5_hash = hashlib.md5()
# Updating the hash object with encoded data
md5_hash.update(data.encode())
# Getting the hexadecimal digest
hash_result = md5_hash.hexdigest()
print("Original String:", data)
print("MD5 Hash:", hash_result)
Output:
Original String: hello world MD5 Hash: 5eb63bbbe01eeed093cb22bb8f5acdc3
Explanation:
- The hashlib module is imported to use the MD5 algorithm.
- The input string “hello world” is converted into bytes using the .encode() method.
- An MD5 hash object is created and the byte data is fed into it using .update().
- The final MD5 hash is generated using .hexdigest(), which returns it in hexadecimal format.
- Time Complexity: O(n) – depends on the length of the input string.
- Space Complexity: O(1) – output size is always fixed at 128 bits (16 bytes).
SHA-1
SHA-1, which stands for Secure Hash Algorithm 1, is a cryptographic hash function designed to take an input message and produce a fixed-size 160-bit (20-byte) hash value. While SHA-1 was once considered secure and widely used, it is now considered vulnerable to collision attacks, and its use is discouraged for security-critical applications.
import hashlib
# Create a sample message to hash
message = "Hello, World!"
# Create a SHA-1 hash object
sha1_hash = hashlib.sha1()
# Update the hash object with the message
sha1_hash.update(message.encode())
# Get the hexadecimal representation of the hash
hashed_message = sha1_hash.hexdigest()
# Print the SHA-1 hash
print("SHA-1 Hash:", hashed_message)
SHA-1 Hash: d3486ae9136e7856bc42212385ea797094475802
Explanation:
The hashlib module provides access to many secure hash algorithms like SHA-1.
The message “Hello, World!” is encoded into bytes using .encode() before hashing.
A SHA-1 hash object is created using hashlib.sha1() and updated with the encoded message.
The hexdigest() function converts the hash to a readable hexadecimal format.
Finally, the resulting hash is printed.
- Time Complexity:O(n) — where n is the length of the message.
- Space Complexity: O(1) — constant space is used to store the hash object and hash value.
SHA-256
SHA-256, part of the SHA-2 family of cryptographic hash functions, is widely used for various security and integrity purposes. It produces a 256-bit (32-byte) hash value, which is considered highly secure.
import hashlib
# Create a sample message to hash
message = "Hello, World!"
# Create a SHA-256 hash object
sha256_hash = hashlib.sha256()
# Update the hash object with the message
sha256_hash.update(message.encode())
# Get the hexadecimal representation of the hash
hashed_message = sha256_hash.hexdigest()
# Print the SHA-256 hash
print("SHA-256 Hash:", hashed_message)
Output:
SHA-256 Hash: a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e
Explanation:
- The hashlib module provides access to SHA-256, a cryptographic hash function.
- The string “Hello, World!” is encoded into bytes before being hashed.
- A SHA-256 hash object is created using hashlib.sha256().
- The update() method feeds the encoded message into the hash function.
- The hexdigest() method returns the hash as a hexadecimal string, which is then printed.
- Time Complexity: O(n), where n is the length of the input message.
- Space Complexity: O(1), as the hash function uses a fixed amount of memory regardless of input size.
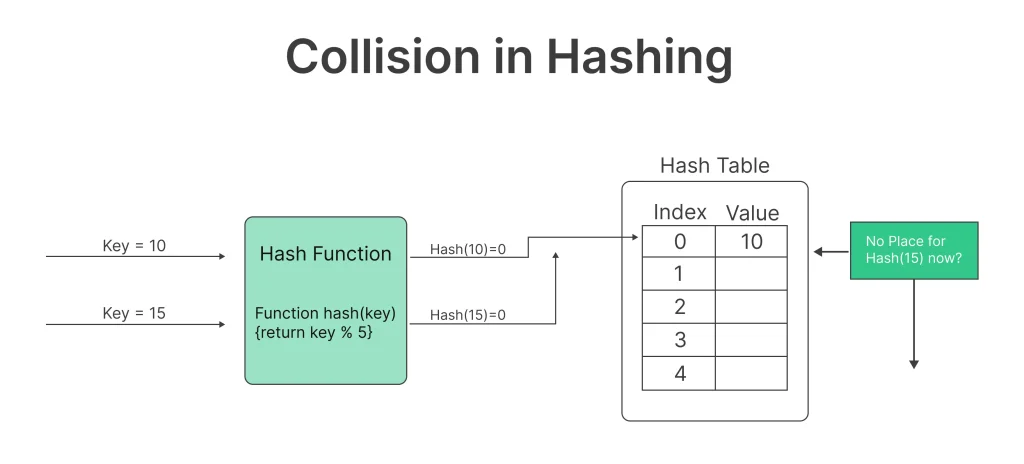
What is collision?
A collision in hashing refers to a situation where two different inputs produce the same hash value or hash code. In other words, it occurs when two distinct sets of data or messages result in identical hash values after undergoing the hashing process.
For Example :
How to handle collision
Handling collisions is a critical aspect of working with hashing algorithms, particularly in data structures and cryptographic applications. There are mainly two methods to handle collision:
- Separate Chaining:
- Open Addressing:
Separate Chaining:
- In this approach, each hash bucket (a location where values are stored) in a hash table contains a linked list or another data structure to hold multiple values that hash to the same location.
- When a collision occurs, the new value is simply added to the list at that location. To retrieve a specific value, you search within the list. This method ensures that all values with the same hash can be stored and retrieved efficiently.
Open Addressing:
- Instead of using separate data structures, open addressing aims to find the next available slot when a collision happens
- There are various open addressing techniques, such as linear probing (checking the next available slot), quadratic probing (using a quadratic function to find the next slot), and double hashing (using a second hash function to calculate the next slot).
- Open addressing can lead to better cache performance compared to separate chaining.
Applications of Hashing
Closing
Introduction to Hashing in Python provide the important informationabout hash functions and their applications in data structures and algorithms. With a deep understanding of hashing, you are better equipped to tackle complex problems and optimize your software, ensuring your place at the forefront of technology and innovation.
FAQs
Hashing is the process of converting data into a fixed-size numerical value (hash). It’s commonly used in data structures like dictionaries and sets for fast lookups and indexing.
The built-in hash() function returns the hash value of an object (like int, str, tuple). It helps store and retrieve data quickly in hash-based collections.
Yes, by overriding the __hash__() and __eq__() methods, you can make custom class instances hashable and usable in sets or as dictionary keys.
No, hash values for strings and objects can vary between different runs due to security features like hash randomization unless explicitly disabled.
Get over 200+ course One Subscription
Courses like AI/ML, Cloud Computing, Ethical Hacking, C, C++, Java, Python, DSA (All Languages), Competitive Coding (All Languages), TCS, Infosys, Wipro, Amazon, DBMS, SQL and others




Login/Signup to comment